Access Control Lists (ACLs)
In this lesson we’re going to be taking a look at Access Control Lists (ACLs). We’ll be discussing how ACLs operate, uses cases and the modes available on Cisco IOS devices.
Exam Topic
5.0 Security
5.1 Configure and verify device access control
5.2 Configure and verify infrastructure security features
5.2.a ACLs
Overview
An Access Control List (ACL) is used to filter traffic on Cisco IOS devices by controlling what traffic is permitted and denied. The ACLs are constructed using a sequential list of access control entries, known as ACEs.
To provide some context, lets take a look at an example of an ACL:
R1#show ip access-lists
Standard IP access list 1
10 permit 192.168.1.0, wildcard bits 0.0.0.255
20 permit 192.168.2.0, wildcard bits 0.0.0.255
30 deny any log
Standard IP access list 1
Indicates our ACL being used to filter traffic.
10 permit 192.168.1.0, wildcard bits 0.0.0.255
20 permit 192.168.2.0, wildcard bits 0.0.0.255
30 deny any log
Indicates our ACEs used within the ACL.
As you can see, instead of using subnet masks, ACLs use wildcard masks in order to identify packets being inspected.
The wildcard mask is used to identify the range of address we want our ACL to match and which we do not.
Wildcard masks act like an inverted subnet mask. You may be familiar with this concept from EIGRP and OSPF configuration.
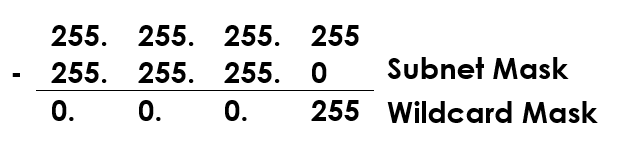
A quick an easy way to calculate the wildcard mask for a network is to subtract the subnet mask from 255.255.255.255.
Subnet Mask – 255.255.255.255 = Wildcard Mask
Lets take a look at some examples:
Example 1
Using the calculation above, let’s work out the wildcard mask for 255.255.255.0.
Example 2
Let’s take a look at another example. This time lets calculate the wildcard mask of 255.255.224.0.

In order for an ACL to operate, they need to be applied to an interface. When applied, we then have to decide if we want the ACL to apply to traffic inbound or outbound on the interface. This is often referred to as ingress (inbound) and egress (outbound).
To better understand this, let’s take a look at an example:
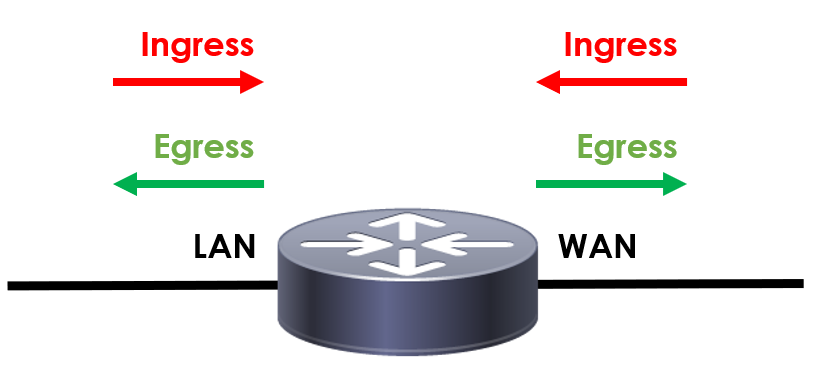
When traffic hits our device and an ACL is in use, the device will attempt to find a rule that matches our traffic. It completes this by working through the rules from top to bottom, until a match has been found.
If no match is found, traffic is denied. This is achieved by an implicit deny at the end of every ACL.
It’s important to note that ACLs are not just used solely for packet filtering, but instead can be used for a list of other functions:
In addition to this, Cisco devices support a number of different ACLs, these include:
We’ll take a look at these different types of ACLs in the upcoming lessons.